Phishing attacks are designed to steal a person’s login and password details so that cyber criminals can take control of social networks, email and online bank accounts. There has been a significant increase in nasty phishing emails recently.
The emails look innocuous enough, mostly containing a button to click to display a message, hinting that the message has been encrypted and you need to click to see it. This usually takes you to a page to put in your login details, so you can see the message.
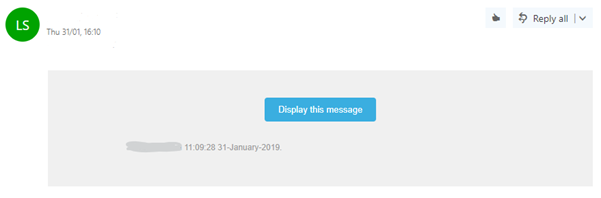
Below is a fairly typical phishing sample email
Sounds all too familiar….if you have clicked on the 'Display Message' button in the email the attackers may now have your account details and could send out hundreds of emails containing the very same piece of malware, both to your address list and to many others.
And so it goes on…..the first most people are aware of it is when they receive a lot of undeliverable email and find that you can't send any email outside the organisation.
Here are 3 tips from the Superhighways tech team.
1. Trust no one
As the famous X-Files saying from the TV show in the early 90s warns, your best strategy is to trust no one.
And your best defence is to ensure to educate all staff, volunteers and your service users NOT to click on any links or attachments in emails that they are not expecting. These emails might come from someone you email often - but you have to ask yourself - why would they want you to click a button or download an attachment you are not expecting?
2. Check it out
If you think the link / attachment is or might be valid, you can test it before clicking it by using a couple of sites to confirm your hunch.
To do this without clicking the link, you need to:
- Hover over the link or button on the email and use the right click on your mouse
- From the option on this right click menu, choose “Copy link address”
- Then paste the URL into an anti-malware check site
The anti-malware check sites we recommend are Kaspersky and Virustotal. Both will verify the link as trustworthy.....or not.
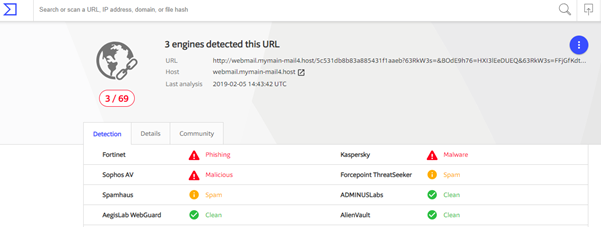
So when you paste the link into either of these two sites, they will confirm or refute your suspicions as you can see from the following screen capture results. Both confirm the site link we checked was a phishing email:
Virustotal results:
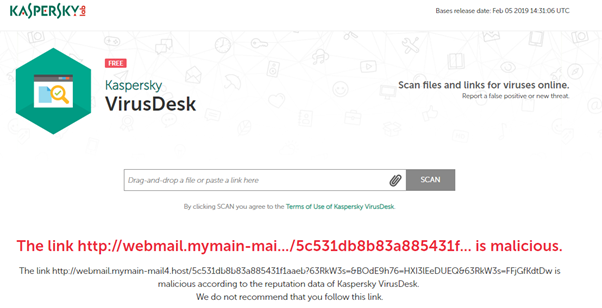
Kaspersky results:
How to check a link that has been shortened
Bitly is one of a few great services to turn your long links into shortened ones.
So, for example, a link to Kingston Digital Health / Digital Health Navigator Training Programme is a long enough title in itself for a post on social media before you even add the link URL http://www.kingstondigitalhealth.org.uk/specialist-training/. If you use Bitly to shorten the link to the training programme it becomes http://bit.ly/KDHtraining.
So if you are in any doubt about a shortened link you receive in an email, you can use check shortened links on this site CheckShortURL and you could then even put in the expanded link into Kaspersky or Virustotal as above.
What about additional malware protection
It is possible to introduce additional levels of protection, but there would be an additional charge for this. If you are using Office 365 you could for example add Microsoft's Advanced Threat Protection. The cost would be £1.51 +VAT per email per month (£18.12 + VAT per email per year).
As you can see this could soon add up if you put it on all your user accounts so user education first is a must - which leads us nicely on to...
3. Train everyone in the organisation to recognise a phishing email
We recommend educating everyone in your organisation to be vigilant and aware of the harm of phishing emails.
We have put together this short video to help spread the word and prevent small charities being caught out by phishing emails.
You can also find further information in the National Cyber Secury Centre's Cyber Security Small Charity Guide
This blog has been produced as part of our Digital Leadership 101 series of training and advice for CEOs and trustees of small charities, funded by the Department of Digital, Culture, Media and Sport and run in partnership with The FSI, NAVCA and London Plus.