The context
In 2019, DCMS (Department of Digital, Culture, Media and Sport) carried out some research and discovered that 52% of charities with an income of £500k or more had identified cyber breaches or attacks in the last 12 months. This figure decreased to 19% for smaller charities with an income of under £100k, but it's assumed that this may be explained by much smaller charities not necessarily idenfitying breaches or attacks, rather than them not happening at all.
We know of many incidents of small charities falling victim of cyber attacks, and anecdotally these seem to have become more frequent since the mass remote working phenomenon as a result of the pandemic.
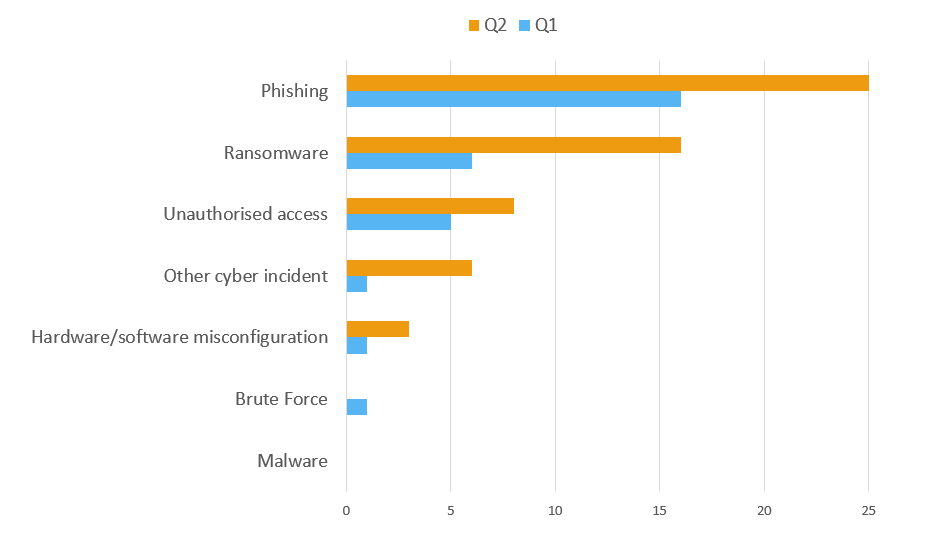
But our experience is also backed up by data published by the Information Commissioner's Office. Look for the Data Security Incident Trends on their website where they share information about data breaches reported to them (remember this is a requirement under GDPR). Below is a chart we've created, filtering this data by the Charity sector, and showing the number of incidents reported by charities to the ICO in Q 1 (April - June) and Q2 (July to September) of 2020. Phishing is the most common cyber security threat, with Ransomware and Unauthorised access next in line. Notice there is a marked increase across all of these areas in Q2.
5 simple steps to protect your small charity
So with this in mind, the National Cyber Security Centre (NCSC) has put together some useful guidance for charities, suggesting we follow 5 quick, simple, free or low cost steps to minimise risks. You can download their full guide here and there's also an infographic which could be useful to share with your team.
We have been running regular training sessions using resources developed by NCSC and NAVCA, and have picked out key areas below.
1) Backing up your data
By taking regular back ups of important data, you're ensuring your charity can still function following the impact of flood, fire, physical damage or theft and you’ll be more resilient to cyber crime.
- Identify what you need to back up - make sure that all essential data for your charities operations is backed up.
- Keep your back up separate - if you are still using e.g. a USB back up device, it's no good keeping this plugged into a PC, as if this is stolen, your back up has gone too! Also, you want to minimise any risk of your back up being damaged e.g. if you have a virus on your computer or network.
- Consider a cloud back up solution. As long as you have a good internet connection, this is a good secure option and relatively low cost. If you are using cloud providers for your data storage and email, back up is likely to be provided as part of this service anyway, but do check any limitations e.g. data only being able to be restored across a certain period of time.
Whatever your solution - it's also important to check that it works! We've come across a number of incidents where organisations think they have a back up solution, but hadn't tested it, and it's failed when they needed to fall back on it.
2) Protecting your charity from Malware
Malware is a term used to reference any kind of malicious software. To protect your organisation's data and systems, make sure you have the following in place:
- Anti virus software that's up to date and with ongoing updates scheduled to happen automatically.
- Firewalls create a buffer zone between a device or network and the internet. Most popular systems include a firewall for free, so make sure this is switched on and you have changed default passwords.
- Prevent users from downloading and installing 'dodgy apps'. As well as policies regarding use of software within your organisation, you can minimise risks associated with accidental download of malicious software by ensuring that users don't have Administrator permissions on their PCs / laptops. Although this means that they will have to ask someone with these permissions when they need to install bona fide applications, it will prevent potential damage from in advertant downloads e.g. from a compromosed website or phishing email, so it's a worthwhile compromise.
- Keeping your operating systems and sofware applications up to date is key as updates often unclude security fixes to protect your devices and systems from known cyber threats. If possible, set these updates to install automatically.
3) Best practice with passwords
- Make sure you switch on password protection AND change all default passwords. There have been instances when hackers have hacked websites or firewalls using the default admin passwords as these hadn't ever been changed
- Avoid predictable passwords - guidance from the NCSC is to choose 3 random words. See how long it takes to crack these example passwords below:
- QwErTy987123! – 15 seconds
- CoffeeTinyFish – 6 hours
- CoffeeTinyFish#9 – 6 days
- Use two factor authentication where this is available. You might already have seen this rolled out e.g. if you have a Gmail or Mailchimp account and you log on from a different device. We are encouraging anyone with an Office 365 account to seriously consider implementing this across your organisations Office 365 account. There is a choice of authentication methods including the authenticator app on your smartphone or a code texted to you each time you log in. Read more about how this step can help prevent 99.9% of account attacks in this Microsoft article.
- Help users cope with ‘password overload’. NCSC guidance is not to enforce frequent password changes as this often results in people choosing simpler, more memorable and therefore less robust passwords. Advice is now actually that it's OK to write your strong password down somewhere as long as you keep it private (and it's not on a post it stuck on to your monitor!) Here is some guidance from NCSC on password managers too.
4) Keeping your smartphones & tablets safe
- Again like with other devices, not all require a password to access the device by default. So the first step is to switch on password protection - a password, pin code or other authentication method might be available.
- Mobile devices can easily become lost or stolen, so it's a good idea to prepare for this eventuality in advance. Check what's available for your devices, as many allow you to:
- track the location of a device
- remotely lock access to the device (to prevent anyone else using it)
- remotely erase the data stored on the device
- retrieve a backup of data stored on the device
- Keep your device and apps up to date. Much like PC or laptop operating systems, tech companies will provide regular updates for devices and apps which might include security patches to identified vulnerabilities, so don't put off installing updates when prompted.
- Use public wifi safely - when we are back travelling around for work and pop into a coffee shop in between meetings, think first about what you'll be doing and whether it's safe to link up to their free wifi. This could just be simpley insecure or at the other extreme, run by criminals. So if you're accessing sensitive client data or making a financial transaction, tethering to your phone's mobile data or using a 3G/4G dongle are more secure options. Or using a Virtual Private Network if this is provided by your organisational IT set up.
NCSC has some guidance on a Bring Your Own Device policy which may be useful, as we know many small charities aren't always in a position to provide organisational devices.
5) Avoiding Phishing attacks
In a typical Phishing attack, scammers send fake emails asking for sensitive information (such as bank details), or containing links to bad websites. They might try to trick you into sending money or steal your details e.g. email addresses or user names and passwords, to sell on to a 3rd party. Take the following steps to avoid falling victim to these increasingly clever attacks:
- Configure accounts to minimise damage that could be caused by preventing an attacker gaining access to as much of your system as possible. Give everyone their own account, making sure they have the ‘least privileges’ needed for their role e.g. only able to access data they need to see. Only give full system access (Adminstrator access) to those who need it. Also use two factor authentication on important accounts, so even if an attacker knows your passwords, they still won’t be able to access that account.
- Think about how you operate as an organisation. Common tricks include sending an invoice for a service that you haven't used, so when the attachment is opened, malware is automatically installed (without your knowledge) on your computer. Another common scam is to trick staff into transferring money or information by sending emails that look authentic. Work with your trustees, staff and volunteers to encourage a healthy sceptcism, review financial procedures, and check with each other in person or by phone before taking a hasty action. Unfortunately we do know of some small London charities who have fallen victim to fraudulent money transfers.
- Educate your staff to know the obvious signs of phishing.
- Check your digital footprint - criminals use publicly available information about organisations and individuals online to make their scam more genuine and arouse less suspicioun. Are you sharing more than you need to?
- Report all attacks:
- Action Fraud - reporting attacks / scams should lead to warnings alerting others
- ICO Breach Notification - report within 72 hours. If you're unsure whether you need to report, you can check via the small organiastion helpline
- Charity Commission - Reporting a Serious Incident (RSI)
- Other Regulators / Funders where applicable